39 an rfid label on a box is an example of what type of physical security detection method?
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging. asset tracking tagging. 12. Which of the following utilities performs sophisticated vulnerability scans, and can identify unencrypted data such as ... Ch 9: Network Risk Management Flashcards Preview - Brainscape An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging 20 What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. 21
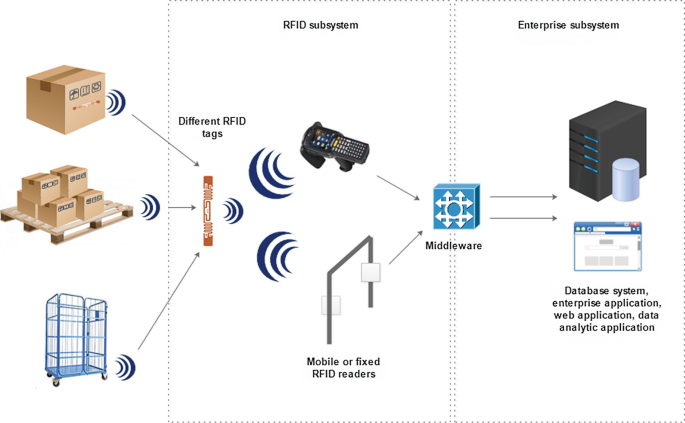
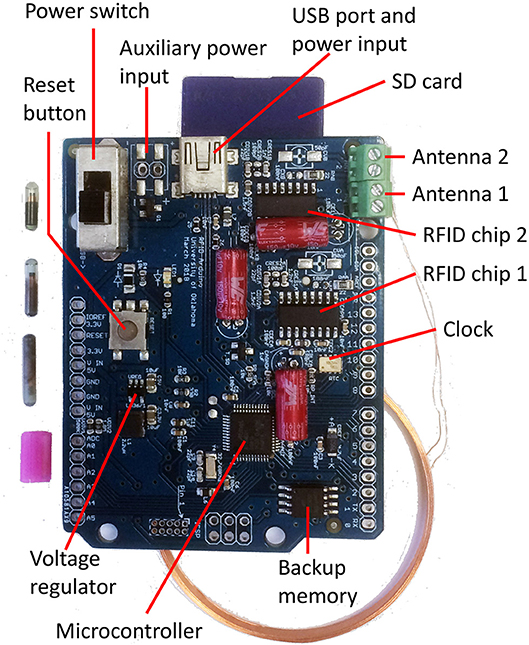
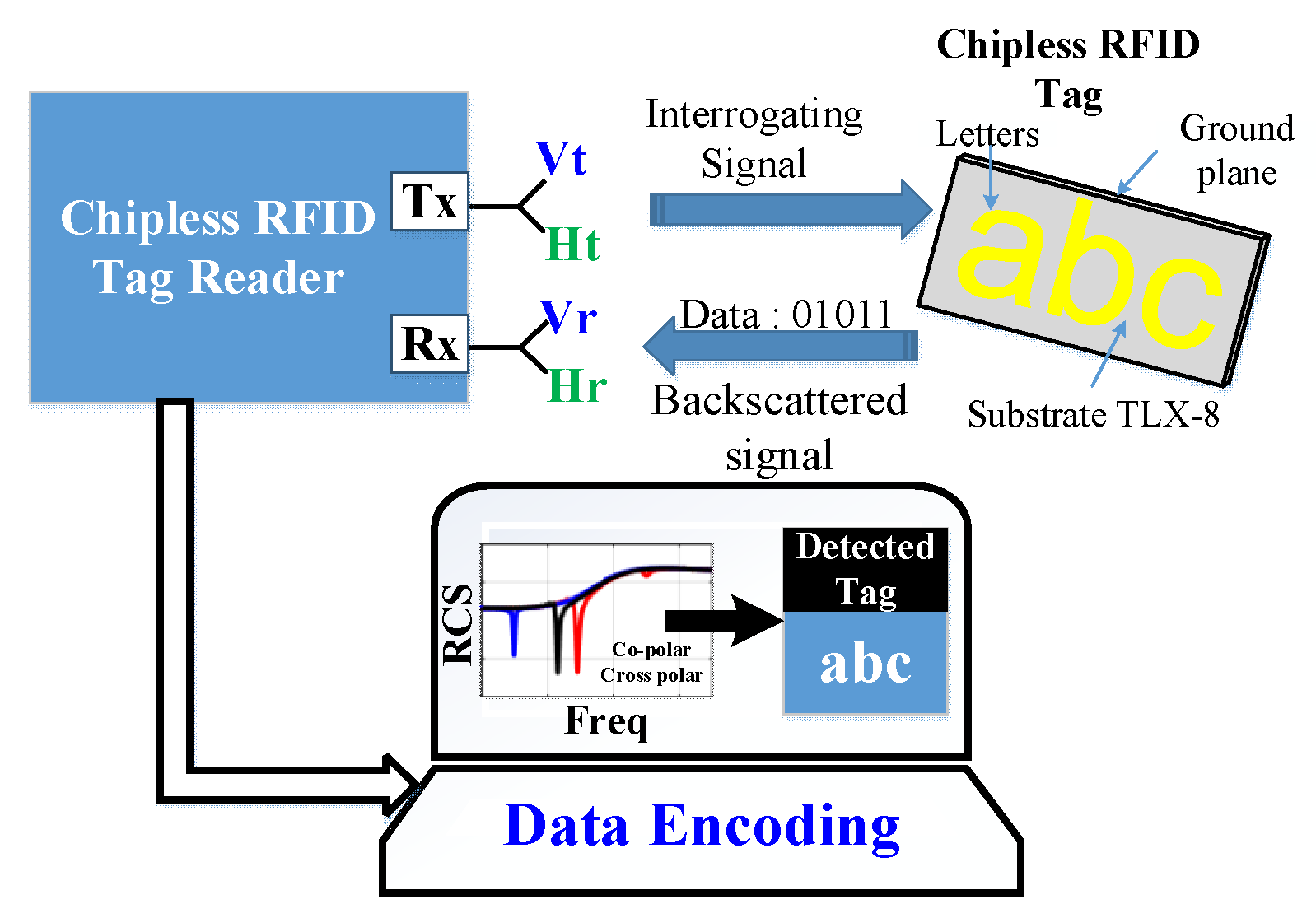
What are RFID Tags, How Do They Work? - Camcode How RFID Tags Work. An RFID tag works by transmitting and receiving information via an antenna and a microchip — also sometimes called an integrated circuit or IC. The microchip on an RFID reader is written with whatever information the user wants. There are two main types of RFID tags: battery-operated and passive.

An rfid label on a box is an example of what type of physical security detection method?
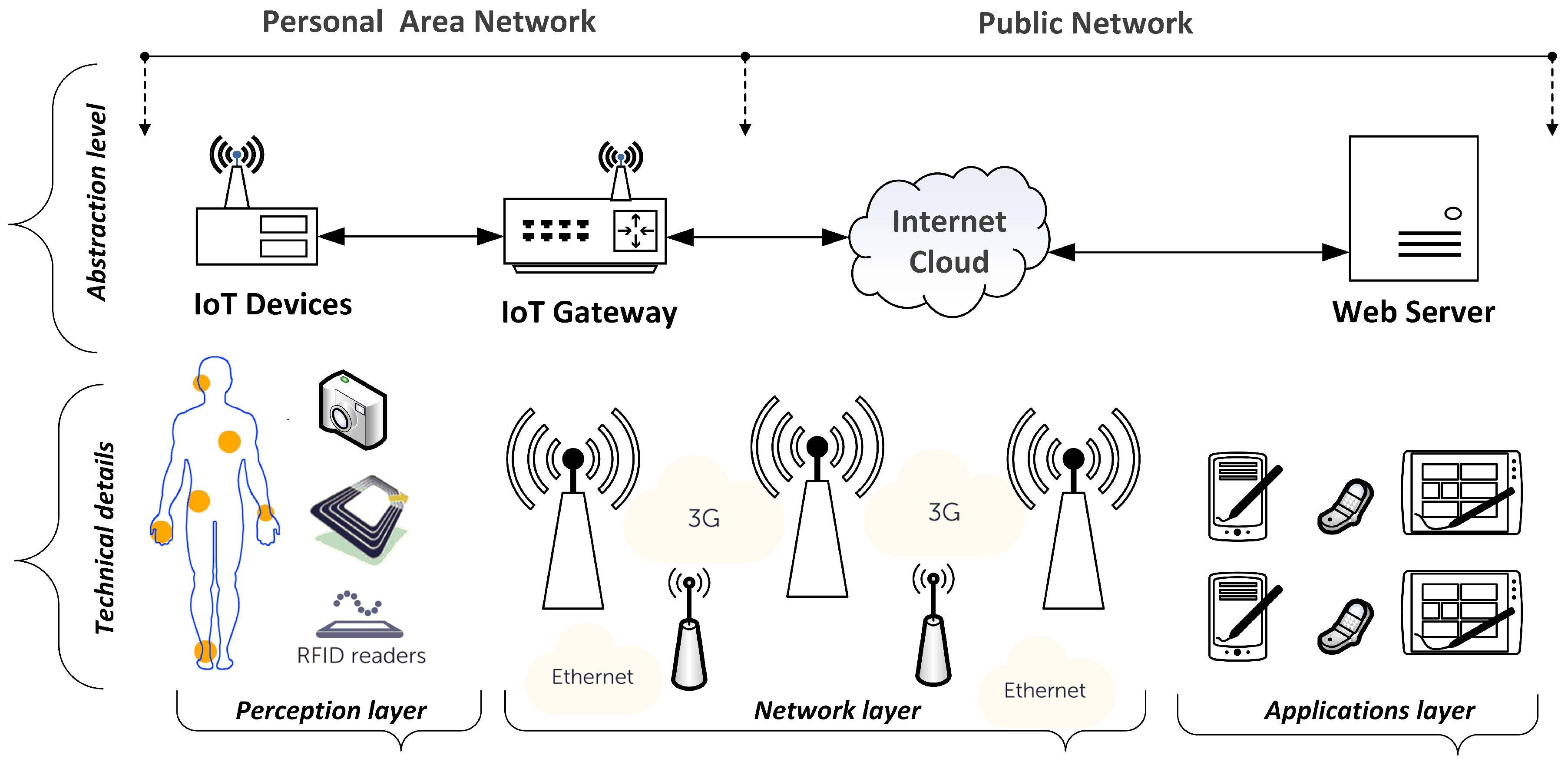
RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database. In open system authentication how does authentication An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging. 75. The combination of a public key and a private key are known by what term below? a. Chapter 9 Flashcards by Victor Mendez | Brainscape An RFID label on a box is an example of what type of physical security detection method? Asset tracking tagging 30 What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths 31
An rfid label on a box is an example of what type of physical security detection method?. What is RFID? | The Beginner's Guide to How RFID Systems Work Recurring costs are attributed to items that are used once and then discarded or consumed during the application. An RFID inlay or label is a common example of a recurring cost in an RFID system. Because of their low-cost, these tags are frequently applied once and kept on an item for its lifespan (or discarded after use). Types and Working Example of RFID Application - ElProCus An RFID Reader. A Processor or a Controller: It can be a host computer with a Microprocessor or a microcontroller which receives the reader input and process the data.; 2 Types of RFID Systems: Active RFID system: These are systems where the tag has its own power source like any external power supply unit or a battery. The only constraint being the life time of the power devices. EOF Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging. d. asset tracking tagging. 12. Which of the following utilities performs sophisticated vulnerability scans, and can identify unencrypted data such ...
What is RFID and how does it work? - IoT Agenda RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. Free Computers Flashcards about Chap 9 and 10 Quiz - StudyStack An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging: What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. Question28 11pts what type of door access control is - Course Hero This preview shows page 11 - 16 out of 16 pages. Question 28 1 / 1 pts What type of door access control is a physical or electronic lock that requires a code in order to open the door? encrypted lock biometric lock Correct! cipher lock. key fob lock Question 29 1 / 1 pts An RFID label on a box is an example of what type of physical security ... Radio Frequency Identification (RFID) | FDA Description. Radio Frequency Identification (RFID) refers to a wireless system comprised of two components: tags and readers. The reader is a device that has one or more antennas that emit radio ...
How do RFID and RF tags work? - Explain that Stuff RF tags use wireless technology. Radio or wireless is a way of transmitting energy through empty space—that is, instead of using a wire cable. The energy is carried by invisible waves of electricity and magnetism that vibrate through the air at the speed of light. The basic science and the practical technology of wireless communication was developed in the second half of the 19th century. Chapter 9 Flashcards by Victor Mendez | Brainscape An RFID label on a box is an example of what type of physical security detection method? Asset tracking tagging 30 What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths 31 In open system authentication how does authentication An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging. 75. The combination of a public key and a private key are known by what term below? a. RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database.






















Post a Comment for "39 an rfid label on a box is an example of what type of physical security detection method?"